Pyramid of Pain
A surprisingly interesting model to determine the level of difficulty an adversary experiences when attempting hide an indicator tracing back to them.
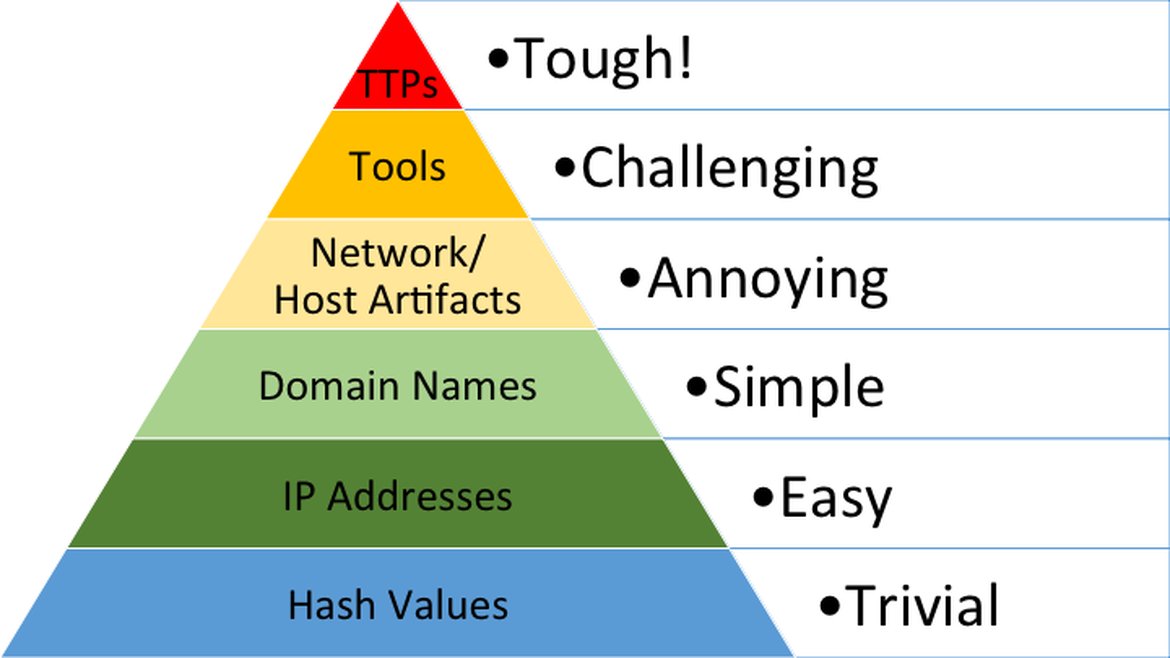
Hash Values
It’s trivial to mutate the hash of a malware often just by changing/appending a byte or two.
IP Addresses
An attacker can easily exchange their IP address for a new one, they can rotate IPs from compromised hosts acting as proxies, and in particularly sophisticated cases employing a fast flux technique.
Fast flux involves rapidly changing IP addresses and/or name servers associated with a domain.
DNS
Purchasing domains is expensive and modifying DNS records can be time consuming, but attackers don’t have to worry too much about this. Registrars often have APIs allowing automation, URL shorteners/redirection are trivial tools attackers can use, and Punycode can confuse victims into trusting a website.
Comparable to typo squatting, Punycode involves creating deceptive Unicode links which is mapped by the browser to a domain the user will not directly see. For example, adıdas.de maps to http://xn--addas-o4a.de/.
Host/Network Artifacts
A fairly broad category that can refer to any traces left by an attacker like registry values, process execution logs, attack patterns, unusual user-agents, and other IOCs.
Fuzzy hashing is included in this category as a way to identify similar files, solving the previously discussed hashing issue. Used by tools liked ssdeep
TTPs (Tactics, Techniques, & Procedures)
Includes the [MITRE ATT&CK Matrix], all steps the adversary may take to achieve their goal. By detecting and responding to these TTPs quickly, attackers will need to reevaluate their approach, potentially moving on to a different target.