This will expand on one of the security domains covered in Cybersecurity - 2. Managing Security Risks, covering the structure of a network, network operations, network attacks, and security hardening practices.
What are networks?
A group of connected devices, ranging from laptops, cell phones, refrigerators, printers, and servers. They have unique address/identifiers to locate each other either over a cable or wirelessly. Two main types:
- LAN (local area network) spanning a small area, the LAN then connects to the internet.
- WAN (wide area network) spanning a large geographical area, the internet can be thought of as a WAN
Devices
Here are some common devices that make up any given network:
- Hub: A network device that broadcasts info to every device on the network, like a radio tower
- Switch: Makes connections between specific devices on the same network by sending and receiving data between them, “controlling the flow of traffic”
- Router: Connects multiple networks together, for example,
Computer -> Router -> Router -> Computer - Modem: Connects router to the internet (an internet service provider), bringing internet access to the LAN, for example
Computer -> Router -> Modem (Internet via ISP) -> Router -> Computer
However, there are also virtualization tools, where these physical devices can have their operations carried out by Cloud service providers.
Cloud networks
To reduce costs, streamline network operations, and increase reliability, companies can now look into third-party providers to manage their networks. It is the practice of using remote servers, applications, and network services hosted on the internet rather than managing local devices. As a result, cloud security has become a more prevalent topic.
Three main categories of services:
- SaaS (Software) - Software suites operated by a provider that can be used remotely by an organization without hosting the software
- IaaS (Infrastructure) - The use of virtual computer components offered by a provider, with pay-as-needed and scalable pricing
- PaaS (Platform) - Refers to tools that application developers can use to design custom apps for their company and business needs
Software defined networks (SDNs) are made of virtual network devices as services, such as switches, routers, firewalls, and more.
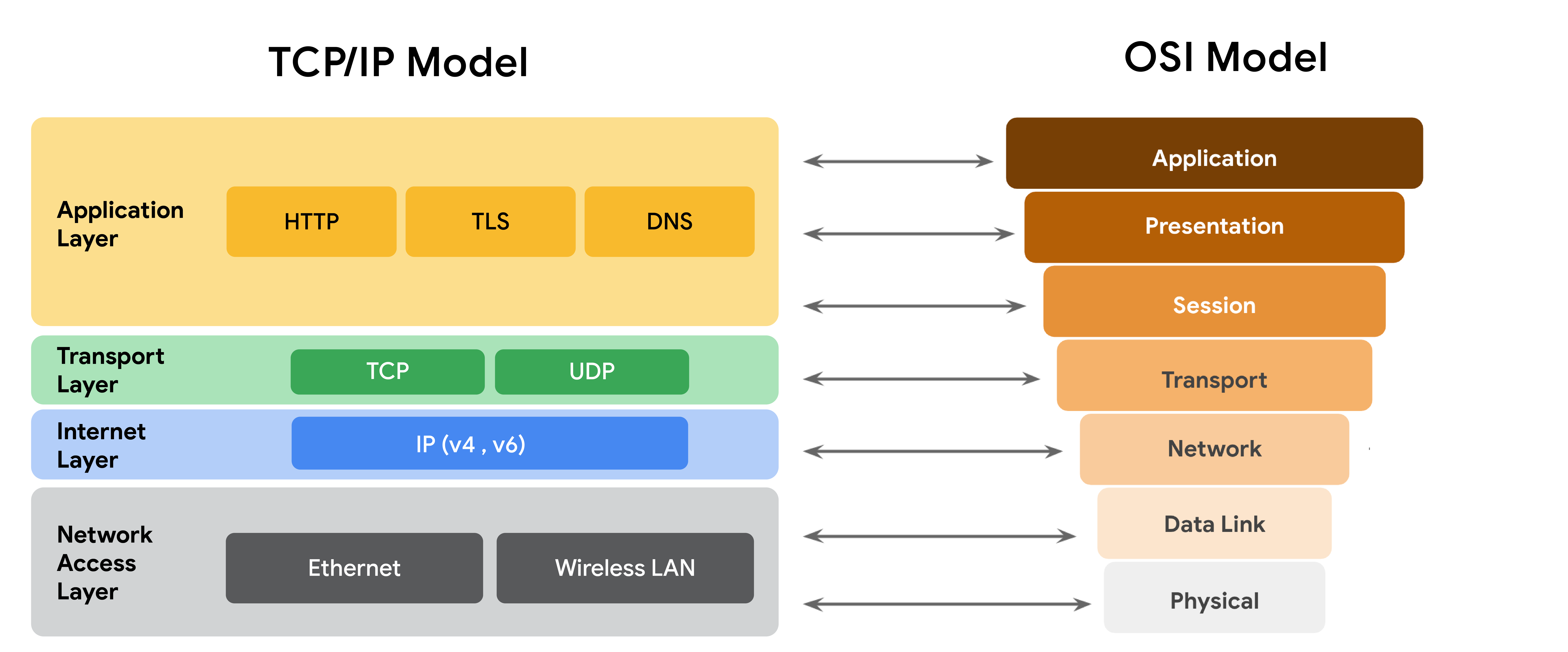
TCP/IP Model
Standing for Transmission Control Protocol and Internet Protocol. TCP allows two devices to form a connection and stream data. IP contains an address, destination MAC address, and protocol to use when communicating. When packets are sent and received, they are assigned a port, a software-defined channel/location that generally indicate “how to process” the packet. Some port examples:
- 25 - email
- 443 - https
- 20 - ftp
The four layers of the TCP/IP model:
- Application Layer (HTTP/TLS/DNS)** - Protocols determine how data packets will interact with receiving devices
- Transport Layer (TCP/UDP) - Protocols to control the flow of traffic across the internet, permitting or denying communication with other devices
- Internet Layer (IP v4, v6) - IP addresses are attached to packets to indicate the locate of the sender and receiver
- Network Access Layer (Ethernet/Wireless LAN) - The creation of data packets and their transmission across a network, hardware like cables and switches
OSI Model
Heavily relates to the TCP/IP model, but provides a more in depth understanding of the processes that occur at each layer.
- Layer 7: Application layer - Processes that involve the every day actions of a user
- Layer 6: Presentation layer - Data translation, encryption, compression, etc.—this replaces low-level data with formats that can be understood by the application layer and therefore the user
- Layer 5: Session layer - Authentication, reconnection, holding a session open, session termination, etc.
- Layer 4: Transport layer - Responsible for delivering raw data between devices, also handles the speed of data transfer, flow of transfer, and chunking/reassembling data
- Layer 3: Network layer - Oversees frames from the data link layer and delivers them to the intended destination, packets allow communication between two networks
- Layer 2: Data link layer - Organizes sending and receiving packets within one network, home to switches on a local network and network interface cards on local devices
- Layer 1: Physical layer - As the name suggests, bit and bobs, hubs, modems, ethernet cables, etc. as a stream of 0s and 1s
Compare the two models here:
Lastly, a word on IP addresses. Private IP addresses are only seen by other devices on the local network, otherwise all devices share one single public facing IP address. MAC addresses are also used which are unique identifier for each physical device, when a switch receives a data packet, it reads the MAC address of the destination device and maps it to a port. This address is placed in a table in the switch which will be referenced when directing packets across the network.
Network Protocols
Communication Protocols
- Transmission Control Protocol (TCP) - Allows two devices to form a connection and stream data via a 3-way handshake. Device sends SYN, server responds SYN/ACK to acknowledge, device sends an ACK to finally establish. Transport Layer.
- User Datagram Protocol (UDP) - A connectionless protocol, it is less reliable with potentially dropped data, but increases the speed of transmission. Transport Layer.
- Hypertext Transfer Protocol (HTTP) - Method of communication between clients and web servers. Application Layer.
- Domain Name System (DNS) - Translates domain name into IP addresses via a dedicated DNS server which returns the corresponding IP address. Port 53, Application Layer.
- Telnet - Used to connect to a remote system, all info is sent in plain text so it is not secure. Port 23, Application Layer.
Management Protocols
- Simple Network Management Protocol (SNMP) - Monitors and manages devices on a network, like password resets on network device or configuration changes. It can also record bandwidth metric from network devices. Application Layer.
- Internet Control Message Protocol (ICMP) - Used by devices to tell each other about data transmission errors. The classically known
pingcommand uses this protocol. Internet Layer. Think of it like a request for a status update from a device - Dynamic Host Configuration Protocol (DHCP) - Works with the router to assign a unique IP address to each device and provide the addresses of the appropriate DNS server. Port 67 (server) / 68 (client, Application Layer.
- Address Resolution Protocol (ARP) - A devices IP address may change over time, so a lot of communication depends on the MAC address. This protocol allows to obtain the MAC address and facilitates translation of an IP address found in a packet to the MAC address. Data Link Layer.
Security Protocols
- (HTTPS) - Expands on HTTP by using sockets layer/transport layer security (SSL/TLS) encryption on all transmissions so they cannot be read. Application Layer.
- Secure File Transfer Protocol (SFTP) - Expands on FTP with secure shell (SSH) which uses AES and other types of encryption to ensure they cannot be read by unintended recipients. Port 22, Application Layer.
- Secure Shell (SSH) - Creates a secure connection with a remote system, a replacement for telnet. Port 22, Application Layer.
Mail Protocols
- Post Office Protocol (POP) - Manages and retrieves email from a mail server. POP3 is the most common usage.
- Internet Message Access Protocol (IMAP) - Used for incoming mail, downloading the header and message content of the email. Mail is kept on the mail server so it can be synced across multiple devices.
- Simple Mail Transfer Protocol (SMTP) - Transmits and routes email from sender to recipient. Regulates how many emails a source can send at a time. Port 25 (unencrypted) and port 587 (encrypted).
Wireless Protocols
Wireless internet is referred to as Wi-Fi, a set of standards that define communication for wireless LANs. The standards are based on the 802.11 family of standards defined by IEEE, commonly referred to as IEEE 802.11. Protocols evolved from WEP to WPA, WPA2, and WPA3.
- Wired Equivalent Privacy (WEP) - Designed to provide the same amount of privacy as if it was a wired network, nowadays it is considered a high-risk security protocol and should be understood.
- Wi-Fi Protected Access (WPA) - An improvement on WEP with backwards compatibility for older hardware. It addressed WEP’s major weakness by using Temporal Key Integrity Protocol (TKIP) which use larger secret keys. It also includes an integrity check, if the transmission was tampered with it will be rejected. It is also considered a high-risk protocol, however, as attackers can use a key reinstallation attack (KRACK) to insert themselves in the WPA authentication handshake and insert a new encryption key.
- WPA2 - Expands on WPA by using AES encryption and use of TKIP. It is considered the security standard for all transmissions today. However, it is still vulnerable to a KRACK attack, this led to the development of WPA3 in 2018.
- WPA3 - Growing in usage, it addresses authentication handshake vulnerability to KRACK attacks, uses Simultaneous Authentication Equals (SAE) to prevent attackers from downloading data from wireless connections to attempt to decode it, and uses 128-bit encryption.
VPNs
A service that changes your public IP address and hides your virtual location to keep your data private. They also encrypt and encapsulate data send across the server. Example of information that is hidden is a MAC address and IP address in a packet.
Security Zones
A segment of a network that protects an internal network from the internet. They control who can access different segments of a network, and can prevent issues from spreading to other parts of a network. For example, a hotel that offers free Wi-Fi may have an unsecure guest network that is kept separate from the encrypted network used by staff.
An organization’s network can be divided into two types of zones: uncontrolled and controlled. An uncontrolled zone would refer to any network out the organization’s control, like the internet.
There are several types of networks within a controlled zone of a subnet. On the outer layer—a DMZ containing public-facing services that can access the internet like web servers, proxy servers, and DNS servers. It serves as a perimeter to the internal network.
Inside the internal network is a restricted zone protecting highly confidential information only accessible to employees with certain privileges.
Subnetting and CIDR
Subnetting is the subdivision of a network into logical groups, such as one for students and one for faculty.
Classless Inter-Domain Routing (CIDR) is a method of assigning subnet masks to IP addresses to create a subnet, as a replacement for classful addressing (a legacy system of IP address classifications from Class A to Class E) to expand the number of available IPv4 addresses as they began to be depleted.
CIDR allows the segmentation of classful networks into smaller chunks. They look like IPv4 addresses but with an appended slash (”/”) followed by a number. 198.51.100.0/24 would encompass all IP addresses in the range 198.51.100.0–198.51.100.255, for example.
Proxy Servers
A proxy server is a dedicated server that sits between the internet and the rest of the internet and fulfills the request of a client by forwarding them to other servers, if the request is safe. It uses a cache to speed up retrieval of frequently accessed information, reducing contact with the internal server.
A forward proxy server regulates and restricts a person’s access to the internet. The goal is to hide a user’s IP address and approve all outgoing requests, essentially forwarding to its destination on the internet. A reverse proxy server regulates and restricts the internet access to an internal server, while preventing the local network’s IP address from being exposed to external parties. An email proxy server filters spam by determining whether a sender’s address was forged, reducing the risk of phishing attacks.
Firewalls
In short, two types: stateful and stateless.
A stateful firewall only requires rules to be configured in one direction (rather than two in stateless), since it uses a state table to track connections, so it can match return traffic to an existing session.
There also exist Next Generation Firewalls (NGFW) which are the most technologically advanced, with intrusion detection features, deep packet inspection, and configuration firewall rules per application. Some with additional features like Malware Sandboxing, Network Anti-Virus, and URL and DNS filtering.
Secure against network intrusions
DoS/DDoS
Floods a server with network traffic with intention of disrupting normal business operations, which can result is financial or time losses. It can potentially leave them vulnerable to other security threats.
A distributed denial of service attack uses multiple devices or servers in different locations making it more likely for the denial of service to succeed.
Three common types:
- SYN flood attack: Initiate numerous TCP connections without completing the handshake process by returning an ACK, leaving the server with many half-open connections.
- ICMP flood attack: Performed by an attacker repeatedly sending ICMP packets to a network server, forcing the server to response with an ICMP packet.
- Ping of death: Sending an oversized ICMP packet larger than 64kb (the maximum size for a correct ICMP packet) repeatedly.
IP Spoofing
Changing the source IP of a data packet to impersonate an authorized system. Some examples:
- On-path attack (man in the middle): An attacker places themselves in the middle of a connection, intercepting and forwarding packets, sometimes altering them.
- Replay attack: Intercepts a data packet and delays or repeats it at another time, used to impersonate an authorized system.
- Smurf attack: A combination of a DDoS and IP spoof by sniffing an authorized user’s IP address and flooding it with packets which overwhelms the target computer.
How do we defend against IP spoofing? Always use encryption so data can’t be read. But also a firewall can deny packets coming from outside the network from a known IP who is inside the network, because that IP should not be coming from outside. I.e. firewall rule rejects all incoming traffic with the same IP as the local network.
Security Hardening
Involves minimizing the attack surface and any other vulnerabilities to keep a network secure. This can be through software, operating systems, networks, applications, databases, hardware, etc. There are also physical protections that can be put in place, like security cameras and guards.
Some common procedures:
- Software updates
- Device application configuration (password resets/requirements)
- Updating encryption standards
- Removing or disabling unnecessary services
- Disabling unused ports
- Reducing access permissions
- Regular penetration testing
OS Hardening
At regular intervals:
- Updates (patch updates)
- Backups
- Hardware and software disposal (wiping all data)
- Implementing a strong password policy
A note on VMs/Sandboxes: It is possible for malware to detect being in a virtual machine, and therefore behave harmlessly to avoid suspicion. Additionally, in rare cases it is possible to escape virtualization through a bug in the VM software.
Network Hardening
At regular intervals:
- Port filtering
- Network access privileges
- Encryption
- Firewall rules maintenance
- Network log analysis
- Backups
- Network segmentation